How To Register A Key On Origin
This browser is no longer supported.
Upgrade to Microsoft Edge to have advantage of the latest features, security updates, and technical support.
Employ SSH key authentication
Azure DevOps Services | Azure DevOps Server 2020 | Azure DevOps Server 2019 | TFS 2018 - TFS 2015
Connect to your Git repos through SSH on macOS, Linux, or Windows to deeply connect using HTTPS authentication. On Windows, we recommended the use of Git Credential Manager or Personal Admission Tokens.
Important
SSH URLs accept changed, only old SSH URLs will go on to work. If you take already set up SSH, you should update your remote URLs to the new format:
- Verify which remotes are using SSH by running
git remote -vin your Git client. - Visit your repository on the web and select the Clone button in the upper correct.
- Select SSH and copy the new SSH URL.
- In your Git client, run:
git remote set-url <remote name, east.k. origin> <new SSH URL>. Alternatively, in Visual Studio, go to Repository Settings, and edit your remotes.
Note
As of Visual Studio 2017, SSH tin be used to connect to Azure DevOps Git repos.
How SSH key authentication works
SSH public fundamental authentication works with an asymmetric pair of generated encryption keys. The public key is shared with Azure DevOps and used to verify the initial ssh connection. The individual primal is kept safe and secure on your system.
Gear up up SSH key authentication
The following steps cover configuration of SSH cardinal authentication on the post-obit platforms:
- Linux
- macOS running at least Leopard (x.5)
- Windows systems running Git for Windows
Configure SSH using the command line. bash is the common shell on Linux and macOS and the Git for Windows installation adds a shortcut to Git Bash in the Start carte du jour. Other beat out environments will work, simply are not covered in this article.
Step i: Create your SSH keys
Note
If you have already created SSH keys on your system, skip this step and get to configuring SSH keys.
The commands here will allow you create new default SSH keys, overwriting existing default keys. Before standing, check your ~/.ssh binder (for case, /habitation/jamal/.ssh or C:\Users\jamal\.ssh) and look for the post-obit files:
- id_rsa
- id_rsa.pub
If these files be, then you have already created SSH keys. You lot tin overwrite the keys with the following commands, or skip this stride and become to configuring SSH keys to reuse these keys.
Create your SSH keys with the ssh-keygen command from the bash prompt. This command will create a 3072-bit RSA key for utilise with SSH. You can requite a passphrase for your private fundamental when prompted—this passphrase provides another layer of security for your individual key. If you requite a passphrase, be sure to configure the SSH agent to enshroud your passphrase and so you lot don't accept to enter it every fourth dimension you connect.
$ ssh-keygen -C "jamal@fabrikam.com" Generating public/individual rsa central pair. Enter file in which to save the central (/c/Users/jamal/.ssh/id_rsa): Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in /c/Users/jamal/.ssh/id_rsa. Your public key has been saved in /c/Users/jamal/.ssh/id_rsa.pub. The cardinal fingerprint is: SHA256:******************************************* jamal@fabrikam.com The key's randomart paradigm is: +---[RSA 3072]----+ |+. +yX*o . | |... ..E+*=o | | ..o.=Eastward=.o | | . * =.o . | | . S o o.. | | + .oo | | S+. . | | ..+.+ | | o*.. | +----[SHA256]-----+ This command produces the two keys needed for SSH authentication: your private key ( id_rsa ) and the public fundamental ( id_rsa.pub ). It is of import to never share the contents of your private key. If the private key is compromised, attackers tin use information technology to trick servers into thinking the connection is coming from yous.
Step two: Add the public key to Azure DevOps Services/TFS
Associate the public key generated in the previous step with your user ID.
-
Open your security settings by browsing to the web portal and selecting your avatar in the upper correct of the user interface. Select SSH public keys in the card that appears.
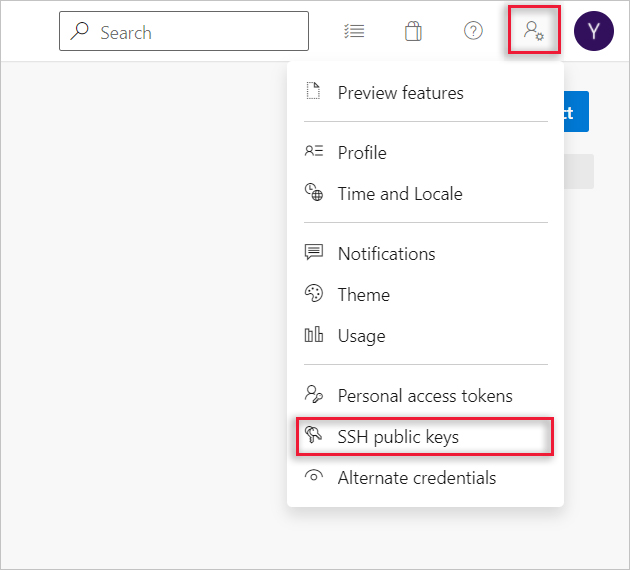
-
Select + New Cardinal.
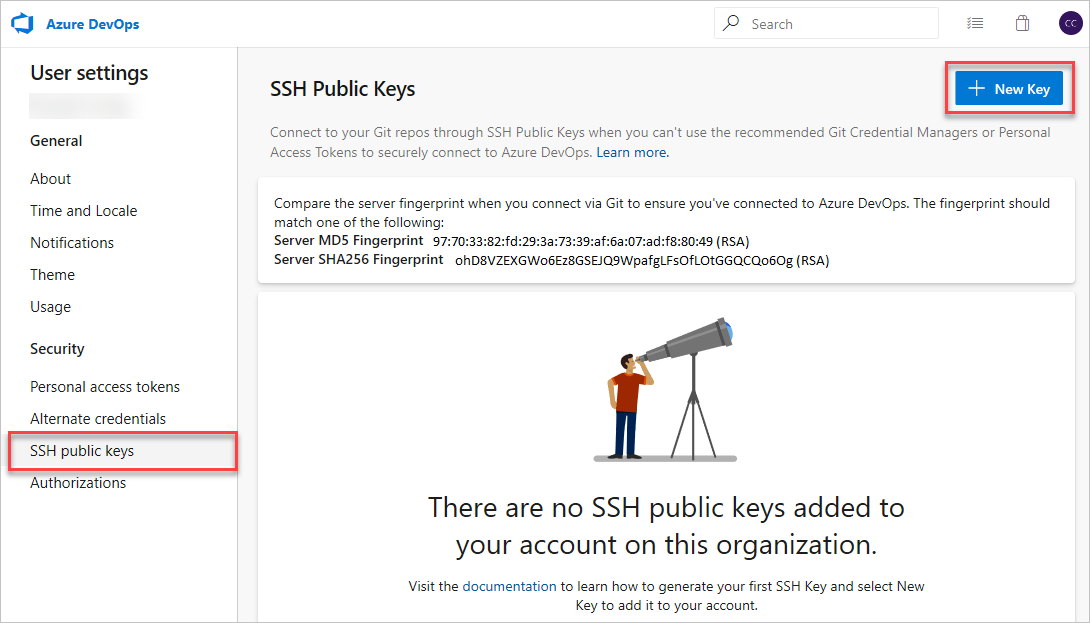
-
Copy the contents of the public key (for example, id_rsa.pub) that you lot generated into the Public Key Data field.
Important
Avoid calculation whitespace or new lines into the Key Data field, as they tin can crusade Azure DevOps Services to apply an invalid public key. When pasting in the key, a newline ofttimes is added at the stop. Be sure to remove this newline if it occurs.

-
Give the key a useful description (this description volition exist displayed on the SSH public keys page for your profile) and then that you lot can remember information technology later. Select Salvage to store the public key. Once saved, you cannot change the key. Y'all can delete the key or create a new entry for some other key. There are no restrictions on how many keys you can add together to your user profile. Besides annotation that SSH keys stored in Azure DevOps expire afterward five years. If your central expires, you may upload a new central or the same i to continue accessing Azure DevOps via SSH.
-
Exam the connection by running the following control:
ssh -T git@ssh.dev.azure.com. If everything is working correctly, you'll receive a response which says:remote: Crush access is non supported.If not, see the department on Questions and troubleshooting.
Pace two: Add the public key to Azure DevOps
Associate the public primal generated in the previous pace with your user ID.
-
Open up your security settings by browsing to the spider web portal and selecting your avatar in the upper right of the user interface. Select Security in the menu that appears.
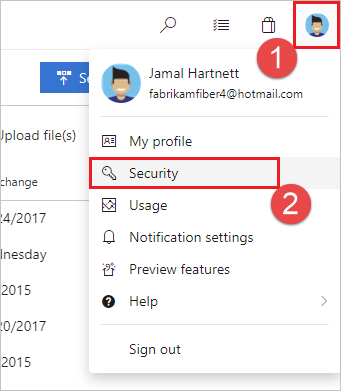
-
Select + New Primal.

-
Re-create the contents of the public central (for example, id_rsa.pub) that you generated into the Public Key Data field.
Of import
Avert adding whitespace or new lines into the Key Information field, as they tin can cause Azure DevOps Services to use an invalid public primal. When pasting in the primal, a newline ofttimes is added at the end. Be sure to remove this newline if it occurs.

-
Give the key a useful description (this description will exist displayed on the SSH public keys page for your profile) and so that you can remember information technology after. Select Save to store the public central. In one case saved, y'all cannot change the central. Yous can delete the key or create a new entry for another key. There are no restrictions on how many keys you can add to your user profile.
-
Test the connection by running the following command:
ssh -T git@ssh.dev.azure.com. If everything is working correctly, you lot'll receive a response which says:remote: Shell admission is non supported.If not, see the department on Questions and troubleshooting.
Pace 3: Clone the Git repository with SSH
-
Copy the SSH clone URL from the spider web portal. In this case, the SSL clone URL is for a repo in an organization named fabrikam-fiber, as indicated by the first role of the URL after
dev.azure.com.
-
Run
git clonefrom the command prompt.git clone git@ssh.dev.azure.com:v3/fabrikam-fiber/FabrikamFiber/FabrikamFiber
SSH may brandish the server's SSH fingerprint and ask you to verify it. You should verify that the displayed fingerprint matches one of the fingerprints in the SSH public keys page.
SSH displays this fingerprint when it connects to an unknown host to protect you lot from man-in-the-middle attacks. Once you take the host's fingerprint, SSH will not prompt you once more unless the fingerprint changes.
$ git clone git@ssh.dev.azure.com:v3/fabrikam-fiber/FabrikamFiber/FabrikamFiber Cloning into 'FabrikamFiber'... The actuality of host 'ssh.dev.azure.com (65.52.8.37)' can't be established. RSA key fingerprint is SHA256:******************************************** Are you sure you want to go on connecting (yes/no)? yep Alert: Permanently added 'ssh.dev.azure.com,65.52.8.37' (RSA) to the list of known hosts. Enter passphrase for cardinal '/c/Users/jamal/.ssh/id_rsa': remote: Azure Repos remote: Institute 127 objects to send. (l ms) Receiving objects: 100% (127/127), 56.67 KiB | two.58 MiB/due south, done. Resolving deltas: 100% (fifteen/xv), done. When you are asked if you lot want to continue connecting, type yes. Git will clone the repo and set up the origin remote to connect with SSH for future Git commands.
Tip
To prevent issues, Windows users should run a command to accept Git reuse their SSH key passphrase.
Questions and troubleshooting
Q: After running git clone, I get the following mistake. What should I do?
Host key verification failed. fatal: Could non read from remote repository. A: Manually tape the SSH key past running: ssh-keyscan -t rsa domain.com >> ~/.ssh/known_hosts
Q: How can I have Git remember the passphrase for my primal on Windows?
A: Run the post-obit command included in Git for Windows to outset upwardly the ssh-agent process in PowerShell or the Windows Command Prompt. ssh-agent will cache your passphrase so you lot don't take to provide information technology every fourth dimension you connect to your repo.
start-ssh-agent.cmd If yous're using the Bash beat out (including Git Bash), start ssh-agent with:
eval `ssh-agent` Q: I use PuTTY every bit my SSH client and generated my keys with PuTTYgen. Tin I apply these keys with Azure DevOps Services?
A: Yep. Load the private key with PuTTYgen, go to Conversions carte and select Export OpenSSH key. Save the private central file and then follow the steps to ready non-default keys. Copy your public central straight from the PuTTYgen window and paste into the Fundamental Data field in your security settings.
Q: How can I verify that the public key I uploaded is the aforementioned fundamental every bit I have locally?
A: You can verify the fingerprint of the public cardinal uploaded with the one displayed in your profile through the following ssh-keygen command run against your public cardinal using the fustigate command line. You will need to change the path and the public primal filename if you are not using the defaults.
ssh-keygen -fifty -Eastward md5 -f ~/.ssh/id_rsa.pub You can then compare the MD5 signature to the ane in your contour. This check is useful if you take connexion problems or take concerns nearly incorrectly pasting in the public primal into the Key Data field when adding the key to Azure DevOps Services.
Q: How can I start using SSH in a repository where I am currently using HTTPS?
A: You'll demand to update the origin remote in Git to modify over from a HTTPS to SSH URL. One time y'all have the SSH clone URL, run the following control:
git remote ready-url origin git@ssh.dev.azure.com:v3/fabrikam-fiber/FabrikamFiber/FabrikamFiber You can now run any Git command that connects to origin.
Q: I'yard using Git LFS with Azure DevOps Services and I go errors when pulling files tracked past Git LFS.
A: Azure DevOps Services currently doesn't support LFS over SSH. Utilize HTTPS to connect to repos with Git LFS tracked files.
Q: How tin can I use a non-default central location, i.e. non ~/.ssh/id_rsa and ~/.ssh/id_rsa.pub?
A: To employ keys created with ssh-keygen in a different place than the default, perform these two tasks:
- The keys must be in a folder that just y'all can read or edit. If the folder has wider permissions, SSH will not apply the keys.
- Yous must let SSH know the location of the keys. You brand SSH aware of keys through the
ssh-add togethercommand, providing the full path to the private key.
ssh-add /home/jamal/.ssh/id_jamal.rsa On Windows, before running ssh-add, you lot volition demand to run the post-obit control from included in Git for Windows:
offset-ssh-amanuensis.cmd This command runs in both PowerShell and the Command Prompt. If yous are using Git Fustigate, the command you need to use is:
eval `ssh-agent` You can discover ssh-add together as office of the Git for Windows distribution and as well run it in any shell surround on Windows.
On macOS and Linux y'all too must have ssh-agent running before running ssh-add, only the command surround on these platforms usually takes intendance of starting ssh-agent for y'all.
Q: I have multiple SSH keys. How do I utilise unlike SSH keys for different SSH servers or repos?
A: By and large, if you configure multiple keys for an SSH client and connect to an SSH server, the client can effort the keys 1 at a time until the server accepts one.
However, this doesn't work with Azure DevOps for technical reasons related to the SSH protocol and how our Git SSH URLs are structured. Azure DevOps will blindly accept the starting time cardinal that the customer provides during hallmark. If that fundamental is invalid for the requested repo, the request will neglect with the following error:
remote: Public key hallmark failed. fatal: Could not read from remote repository.
For Azure DevOps, yous'll need to configure SSH to explicitly use a specific cardinal file. One way to do this to edit your ~/.ssh/config file (for case, /dwelling/jamal/.ssh or C:\Users\jamal\.ssh) every bit follows:
# The settings in each Host section are applied to any Git SSH remote URL with a # matching hostname. # Generally: # * SSH uses the start matching line for each parameter proper name, eastward.g. if there's # multiple values for a parameter across multiple matching Host sections # * "IdentitiesOnly yes" prevents keys cached in ssh-agent from being tried before # the IdentityFile values we explicitly set. # * On Windows, ~/.ssh/your_private_key maps to %USERPROFILE%\.ssh\your_private_key, # east.m. C:\Users\<username>\.ssh\your_private_key. # Well-nigh common scenario: to use the same fundamental beyond all hosted Azure DevOps # organizations, add together a Host entry like this: Host ssh.dev.azure.com IdentityFile ~/.ssh/your_private_key IdentitiesOnly yes # This model volition also work if you still use the older SSH URLs with a # hostname of vs-ssh.visualstudio.com: Host vs-ssh.visualstudio.com IdentityFile ~/.ssh/your_private_key IdentitiesOnly yes # Less mutual scenario: if you need unlike keys for different organizations, # yous'll need to use host aliases to create separate Host sections. # This is because all hosted Azure DevOps URLs have the aforementioned hostname # (ssh.dev.azure.com), so SSH has no fashion to distinguish them by default. # # Imagine that we have the following two SSH URLs: # * git@ssh.dev.azure.com:v3/Fabrikam/Project1/fab_repo # * For this, we want to apply `fabrikamkey`, so we'll create `devops_fabrikam` equally # a Host allonym and tell SSH to use `fabrikamkey`. # * git@ssh.dev.azure.com:v3/Contoso/Project2/con_repo # * For this, we want to use `contosokey`, and so nosotros'll create `devops_contoso` equally # a Host alias and tell SSH to use `contosokey`. # # To set explicit keys for the 2 host aliases and to tell SSH to utilize the right # actual hostname, add the next two Host sections: Host devops_fabrikam HostName ssh.dev.azure.com IdentityFile ~/.ssh/private_key_for_fabrikam IdentitiesOnly yes Host devops_contoso HostName ssh.dev.azure.com IdentityFile ~/.ssh/private_key_for_contoso IdentitiesOnly yes # # And then, instead of using the existent URLs, tell Git yous desire to utilise these URLs: # * git@devops_fabrikam:v3/Fabrikam/Project1/fab_repo # * git@devops_contoso:v3/Contoso/Project2/con_repo # # At the cease of the file, you can put global defaults for other SSH hosts you # may connect to. Note that "*" also matches any hosts that friction match the sections # above, and retrieve that SSH uses the starting time matching line for each parameter proper name. Host * # The settings in each Host section are applied to any Git SSH remote URL with a # matching hostname. # Generally: # * SSH uses the kickoff matching line for each parameter proper noun, e.g. if there's # multiple values for a parameter across multiple matching Host sections # * "IdentitiesOnly yeah" prevents keys cached in ssh-amanuensis from existence tried earlier # the IdentityFile values we explicitly set. # * On Windows, ~/.ssh/your_private_key maps to %USERPROFILE%\.ssh\your_private_key, # due east.yard. C:\Users\<username>\.ssh\your_private_key. # Say your on-bounds Azure DevOps Server instance has SSH URLs like this: # ssh://someHost:22/someCollection/some_project/_git/some_repo # Add the post-obit Host section: Host someHost IdentityFile ~/.ssh/your_private_key IdentitiesOnly aye # At the end of the file, you can put global defaults for other SSH hosts you # may connect to. Note that "*" also matches any hosts that lucifer the sections # above, and remember that SSH uses the first matching line for each parameter name. Host * Q: How exercise I fix errors that mention "no matching key exchange method establish"?
A: Git for Windows 2.25.1 shipped with a new version of OpenSSH which removed some key exchange protocols by default. Specifically, diffie-hellman-group14-sha1 has been identified as problematic for some Azure DevOps Server and TFS customers. Y'all tin can piece of work around the problem by adding the following to your SSH configuration (~/.ssh/config):
Host <your-azure-devops-host> KexAlgorithms +diffie-hellman-group14-sha1 Replace <your-azure-devops-host> with the hostname of your Azure DevOps or TFS server, like tfs.mycompany.com.
Q: What notifications may I receive virtually my SSH keys?
A: Whenever you lot register a new SSH Fundamental with Azure DevOps Services, you will receive an email notification informing you that a new SSH central has been added to your business relationship.
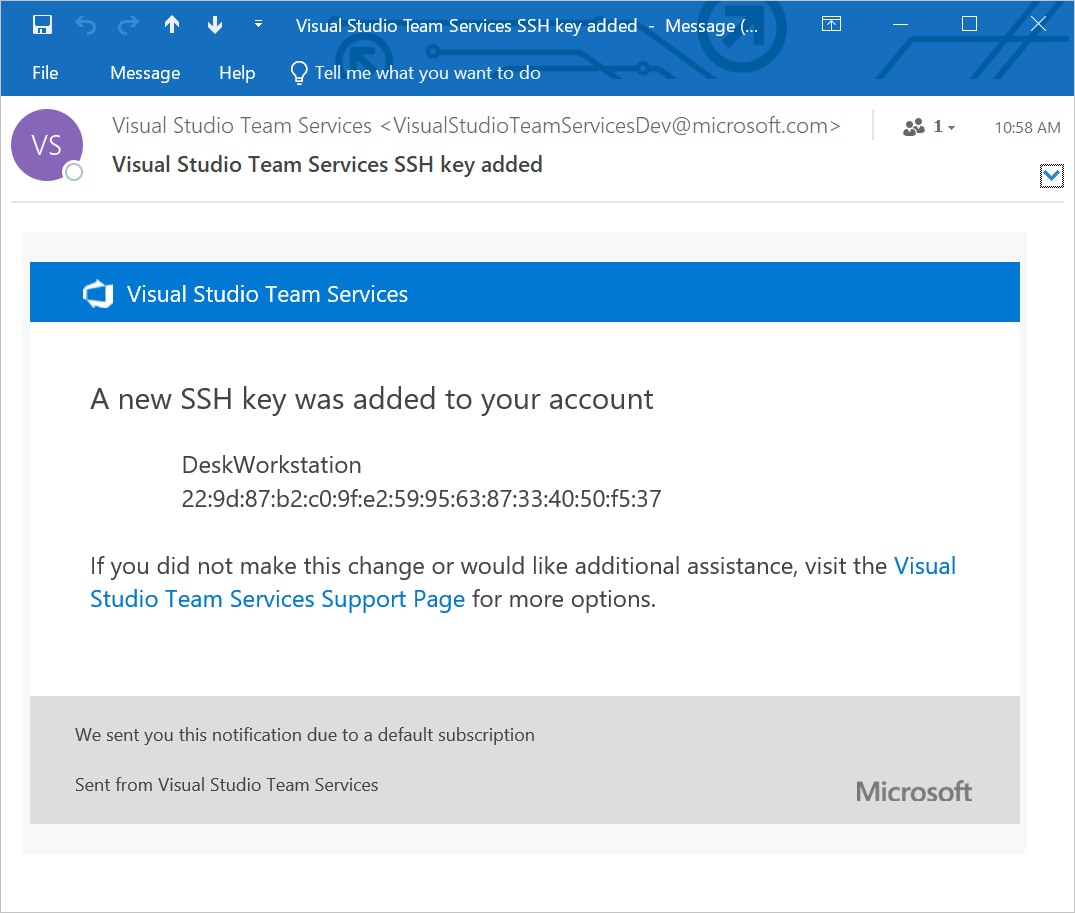
Q: What exercise I do if I believe that someone other than me is adding SSH keys on my account?
A: If you receive a notification of an SSH key being registered and you did not manually upload it to the service, your credentials may take been compromised.
The next step would be to investigate whether or not your password has been compromised. Irresolute your password is always a skilful first pace to defend confronting this attack vector. If you're an Azure Active Directory user, talk with your administrator to check if your account was used from an unknown source/location.
Q: What exercise I exercise if I'k still prompted for my countersign and GIT_SSH_COMMAND="ssh -v" git fetch shows no mutual signature algorithm?
A: Some Linux distributions, such as Fedora Linux, have crypto policies that require stronger SSH signature algorithms than Azure DevOps supports (as of January 2021). In that location'southward an open feature asking to add this support.
You can piece of work effectually the issue by adding the following lawmaking to your SSH configuration (~/.ssh/config):
Host ssh.dev.azure.com PubkeyAcceptedKeyTypes=ssh-rsa Replace ssh.dev.azure.com with the right host name if y'all use Azure DevOps Server.
Feedback
Submit and view feedback for
Source: https://docs.microsoft.com/en-us/azure/devops/repos/git/use-ssh-keys-to-authenticate?view=azure-devops
Posted by: hooperseliesser.blogspot.com


0 Response to "How To Register A Key On Origin"
Post a Comment